
Security is a Priority
AMD drives innovation in high-performance computing, graphics, and visualization technologies - the building blocks for gaming, immersive platforms, cloud and datacenters. Security is a priority consideration from the moment our products are conceived, including intensive security reviews during the hardware and software development process.
Throughout the lifetime of a product, AMD seeks more efficient ways to make our products more secure, including working closely with partners, academics, researchers, and end users in the ecosystem. As a CNA (CVE Numbering Authority) member we follow coordinated vulnerability disclosure practices and seek to respond quickly and appropriately to reported issues.

As members of FIRST (Forum of Incident Response and Security Teams) our PSIRT team is trained to respond systematically to potential issues reported to AMD.
AMD also recommends users follow security best practices, including keeping your operating system up-to-date, running the latest versions of firmware and software, and regularly running antivirus software.

Security Bulletins and Briefs
Product Security Bulletins and Briefs are listed below. Click on the Title link in the table to view more details.
- Security Bulletins: Used to communicate mitigations or guidance for newly published CVEs.
- Security Briefs: Used to inform of potential vulnerabilities where no CVE(s) have been issued by AMD and/or to provide additional communication regarding previously published potential vulnerabilities where AMD has provided prior guidance.
NOTE: An issuance of a Security Brief by AMD is not necessarily an acknowledgement that AMD products are impacted, e.g. Security Briefs may include AMD communication regarding researcher findings where AMD believes there is no product impact.
| AMD ID | Title | Type | CVEs | Published Date | Last Updated Date |
|---|---|---|---|---|---|
| AMD-SB-7029 | AMD Transient Scheduler Attacks | Security Bulletin | CVE-2024-36350, CVE-2024-36357, CVE-2024-36348, CVE-2024-36349 | Jul 08, 2025 | Jul 08, 2025 |
| AMD-SB-8008 | Zynq™ UltraScale+™ SoC Overwriting Protected Memory Regions Through PMU Firmware | Security Bulletin | CVE-2025-0038 | Jul 01, 2025 | Jul 01, 2025 |
| AMD-SB-6013 | Uninitialized GPU Register Access | Security Bulletin | CVE-2024-21969 | Aug 13, 2024 | Jun 23, 2025 |
| AMD-SB-4007 | DXE Driver Memory Leaks | Security Bulletin | CVE-2023-20594, CVE-2023-20597 | Sep 20, 2023 | Jun 23, 2025 |
| AMD-SB-6010 | GPU Memory Leaks | Security Bulletin | CVE-2023-4969 | Jan 16, 2024 | Jun 23, 2025 |
| AMD-SB-7039 | Unauthorized Access to AMD Secure Processor’s Crypto-Co-Processor | Security Bulletin | CVE-2023-20599 | Jun 10, 2025 | Jun 10, 2025 |
| AMD-SB-4011 | TPM Reference Implementation | Security Bulletin | CVE-2025-2884 | Jun 10, 2025 | Jun 10, 2025 |
| AMD-SB-3019 | AMD SEV Confidential Computing Vulnerability | Security Bulletin | CVE-2024-56161 | Feb 03, 2025 | Jun 10, 2025 |
| AMD-SB-6019 | CROSS-PROCESS GPU MEMORY DISCLOSURE | Security Bulletin | CVE-2024-36353 | Feb 25, 2025 | Jun 10, 2025 |
| AMD-SB-3010 | Cache-based Side-Channel Attack Against SEV | Security Bulletin | N/A | Feb 03, 2025 | Jun 03, 2025 |
| AMD-SB-8010 | Versal Adaptive SoC – Overwriting Protected Memory Regions through PLM Firmware | Security Bulletin | CVE-2025-0037 | Jun 03, 2025 | Jun 03, 2025 |
| AMD-SB-8011 | Versal™ Adaptive SoC – Improper Configuration of the Secure Stream Switch during Post-Boot Cryptographic Operations | Security Bulletin | CVE-2025-0036 | Jun 03, 2025 | Jun 03, 2025 |
| AMD-SB-7033 | AMD CPU Microcode Signature Verification Vulnerability | Security Bulletin | CVE-2024-36347 | Mar 05, 2025 | Jun 03, 2025 |
| AMD-SB-7042 | IOLeak - CPU Side Channel Attacks | Security Brief | N/A | May 22, 2025 | May 22, 2025 |
| AMD-SB-9014 | AMD Optimizing CPU Libraries (AOCL) Vulnerabilities | Security Bulletin | CVE-2024-21960, CVE-2024-36339 | May 13, 2025 | May 13, 2025 |
| AMD-SB-9013 | AMD uProf Vulnerability | Security Bulletin | CVE-2024-36340 | May 13, 2025 | May 13, 2025 |
| AMD-SB-9015 | AMD Manageability Tools Vulnerabilities | Security Bulletin | CVE-2024-36321, CVE-2025-0035, CVE-2023-31358, CVE-2023-31359 | May 13, 2025 | May 13, 2025 |
| AMD-SB-7030 | Privilege Desynchronization: Cross-Privilege Spectre Attacks with Branch Privilege Injection | Security Brief | N/A | May 13, 2025 | May 13, 2025 |
| AMD-SB-7034 | Spectre-v2 Domain Isolation | Security Brief | N/A | May 13, 2025 | May 13, 2025 |
| AMD-SB-8005 | Potential Vulnerabilities When Deviating From ARM® AXI Standard Protocol | Security Brief | N/A | Oct 30, 2024 | Apr 21, 2025 |
| AMD-SB-8007 | Spectre-Branch Status Eviction (BSE) Vulnerability on ARM® Processors | Security Brief | CVE-2024-10929 | Apr 10, 2025 | Apr 10, 2025 |
| AMD-SB-7027 | AMD SMM Vulnerabilities | Security Bulletin | CVE-2024-0179, CVE-2024-21925 | Feb 11, 2025 | Apr 07, 2025 |
| AMD-SB-7037 | AMD Ryzen™ AI Software Vulnerabilities | Security Bulletin | CVE-2025-0014, CVE-2024-36337, CVE-2024-36328, CVE-2024-36336 | Apr 02, 2025 | Apr 02, 2025 |
| AMD-SB-7026 | Branch History Leak | Security Brief | N/A | Mar 27, 2025 | Mar 27, 2025 |
| AMD-SB-6008 | AMD Graphics Driver Vulnerabilities – February 2025 | Security Bulletin | CVE-2024-21971, CVE-2023-20508 | Feb 11, 2025 | Mar 21, 2025 |
| AMD-SB-7040 | PAGE PREFETCHER ATTACK | Security Brief | N/A | Feb 28, 2025 | Feb 28, 2025 |
| AMD-SB-6021 | AMD Graphics Driver for Linux® | Security Bulletin | CVE-2023-52921, CVE-2024-41008, CVE-2024-26656, CVE-2024-26657, CVE-2024-27400 | Feb 25, 2025 | Feb 25, 2025 |
| AMD-SB-6005 | AMD Graphics Driver Vulnerabilities – August 2024 | Security Bulletin | CVE-2021-26367, CVE-2023-20509, CVE-2023-31310, CVE-2023-20510, CVE-2023-20513, CVE-2023-31304, CVE-2023-31307, CVE-2023-20512, CVE-2023-31305 | Aug 13, 2024 | Feb 17, 2025 |
| AMD-SB-6016 | AMD GPU Security Vulnerabilities | Security Bulletin | CVE-2024-21936, CVE-2024-21927, CVE-2024-21935 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-7028 | AMD SMM Callout Vulnerability | Security Bulletin | CVE-2024-21924 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-5004 | AMD Embedded Processors Vulnerabilities – February 2025 | Security Bulletin | CVE-2023-31342, CVE-2023-31343, CVE-2023-31345, CVE-2023-31352, CVE-2023-20515, CVE-2023-20582, CVE-2023-31356, CVE-2023-31331, CVE-2023-20581, CVE-2023-20507 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-7032 | Last-Level Cache Attack | Security Brief | N/A | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-9008 | AMD DASH CLI Incorrect Default Permissions Vulnerability | Security Bulletin | CVE-2024-21968 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-4008 | AMD Client Processor Vulnerabilities – February 2025 | Security Bulletin | CVE-2023-31342, CVE-2023-31343, CVE-2023-31345, CVE-2023-20515, CVE-2023-31331, CVE-2023-20507 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-9012 | AIM-T Manageability Service Vulnerabilities | Security Bulletin | CVE-2023-31360, CVE-2023-31361 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-9010 | AMD Ryzen™ Master Utility DLL Hijacking Vulnerability | Security Bulletin | CVE-2024-21966 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-3009 | AMD Server Processor Vulnerabilities – February 2025 | Security Bulletin | CVE-2023-31342, CVE-2023-31343, CVE-2023-31345, CVE-2023-31352, CVE-2023-20582, CVE-2023-20581 | Feb 11, 2025 | Feb 11, 2025 |
| AMD-SB-6015 | AMD Graphics Driver Installer Vulnerability | Security Bulletin | CVE-2024-21937 | Nov 12, 2024 | Dec 19, 2024 |
| AMD-SB-3015 | Undermining Integrity Features of SEV-SNP with Memory Aliasing | Security Bulletin | CVE-2024-21944 | Dec 10, 2024 | Dec 10, 2024 |
| AMD-SB-3012 | QEMU Root Shell Access Vulnerability | Security Bulletin | N/A | Dec 09, 2024 | Dec 09, 2024 |
| AMD-SB-7005 | Return Address Security Bulletin | Security Bulletin | CVE-2023-20569 | Aug 08, 2023 | Dec 05, 2024 |
| AMD-SB-7014 | SMM Lock Bypass | Security Bulletin | CVE-2023-31315 | Aug 09, 2024 | Nov 18, 2024 |
| AMD-SB-3011 | Guest Memory Vulnerabilities | Security Bulletin | CVE-2023-31355, CVE-2024-21978, CVE-2024-21980 | Aug 05, 2024 | Nov 18, 2024 |
| AMD-SB-9003 | AMD Management Console Incorrect Default Permissions Vulnerability | Security Bulletin | CVE-2024-21957 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-9006 | AMD Cloud Manageability Service Incorrect Default Permissions Vulnerability | Security Bulletin | CVE-2024-21939 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-9007 | AMD Provisioning Console Incorrect Default Permissions Vulnerability | Security Bulletin | CVE-2024-21958 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-9004 | Ryzen™ Master Monitoring SDK & AMD Ryzen™ Master Utility Incorrect Default Permission Vulnerabilities | Security Bulletin | CVE-2024-21945, CVE-2024-21946 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-7017 | AMD Ryzen™ AI Software | Security Bulletin | CVE-2024-21949, CVE-2024-21974, CVE-2024-21975, CVE-2024-21976 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-9005 | AMD Management Plugin for SCCM Incorrect Default Permissions Vulnerability | Security Bulletin | CVE-2024-21938 | Nov 12, 2024 | Nov 12, 2024 |
| AMD-SB-7031 | Return Address Stack Side Channel | Security Brief | N/A | Nov 07, 2024 | Nov 07, 2024 |
| AMD-SB-7025 | Microarchitectural Cache Side-Channel Attacks | Security Brief | N/A | Oct 14, 2024 | Oct 30, 2024 |
| AMD-SB-7023 | State Injection Into Hardware Prefetchers | Security Brief | N/A | Oct 18, 2024 | Oct 18, 2024 |
| AMD-SB-3013 | Performance Counter Side Channel | Security Brief | N/A | Oct 14, 2024 | Oct 14, 2024 |
| AMD-SB-6012 | Radeon™ Driver for DirectX® 11 Shader Vulnerabilities | Security Bulletin | CVE-2024-21972, CVE-2024-21979 | Apr 09, 2024 | Aug 19, 2024 |
| AMD-SB-9001 | AMD µPROF Security Notice | Security Bulletin | CVE-2023-31348, CVE-2023-31349, CVE-2023-31341, CVE-2023-31366 | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-8003 | Out of Bounds Read in Arm® Trusted Firmware | Security Bulletin | CVE-2023-31339 | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-7024 | Efficient Instruction Cache Attacks via Self-Modifying Code Conflicts | Security Brief | N/A | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-4004 | Client Vulnerabilities – Aug 2024 | Security Bulletin | CVE-2022-23815, CVE-2023-20578, CVE-2021-26344, CVE-2022-23817, CVE-2021-26367, CVE-2024-21981, CVE-2021-46746, CVE-2021-26387, CVE-2021-46772, CVE-2023-20518 | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-3003 | AMD Server Vulnerabilities – August 2024 | Security Bulletin | CVE-2023-20578, CVE-2021-26344, CVE-2023-20591, CVE-2024-21981, CVE-2023-20584, CVE-2021-46746, CVE-2023-31356, CVE-2021-26387, CVE-2021-46772, CVE-2023-20518 | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-5002 | AMD Embedded Processors Vulnerabilities – Aug 2024 | Security Bulletin | CVE-2022-23815, CVE-2023-20578, CVE-2021-26344, CVE-2022-23817, CVE-2023-20591, CVE-2021-26367, CVE-2024-21981, CVE-2021-46746, CVE-2021-26387, CVE-2021-46772, CVE-2023-20518 | Aug 13, 2024 | Aug 13, 2024 |
| AMD-SB-7009 | AMD Processor Vulnerabilities | Security Bulletin | CVE-2023-20576, CVE-2023-20577, CVE-2023-20579, CVE-2023-20587 | Feb 13, 2024 | Jun 13, 2024 |
| AMD-SB-1041 | SPI Lock Bypass | Security Bulletin | CVE-2022-23829 | Jun 11, 2024 | Jun 11, 2024 |
| AMD-SB-7008 | Cross-Process Information Leak | Security Bulletin | CVE-2023-20593 | Jul 24, 2023 | Apr 30, 2024 |
| AMD-SB-7015 | Exploiting the Conditional Branch Predictor | Security Brief | N/A | Apr 26, 2024 | Apr 26, 2024 |
| AMD-SB-7019 | Last-Level Cache Side-Channel Attacks | Security Brief | N/A | Apr 26, 2024 | Apr 26, 2024 |
| AMD-SB-7021 | AMD Response to “ZENHAMMER: Rowhammer Attacks on AMD Zen-Based Platforms” | Security Brief | N/A | Mar 25, 2024 | Apr 09, 2024 |
| AMD-SB-7018 | Spectre V2 Mitigation Bypass on Linux® | Security Bulletin | CVE-2024-2201 | Apr 09, 2024 | Apr 09, 2024 |
| AMD-SB-3008 | Disrupting AMD SEV-SNP on Linux® With Interrupts | Security Bulletin | CVE-2024-25742, CVE-2024-25743, CVE-2024-25744 | Apr 05, 2024 | Apr 05, 2024 |
| AMD-SB-7016 | Speculative Race Conditions (SRCs) | Security Brief | CVE-2024-2193 | Mar 12, 2024 | Mar 12, 2024 |
| AMD-SB-6011 | WebGPU Browser-based GPU Cache Side-Channel | Security Brief | N/A | Mar 12, 2024 | Mar 12, 2024 |
| AMD-SB-1000 | AMD Graphics Driver for Windows 10 | Security Bulletin | CVE-2020-12902, CVE-2020-12891, CVE-2020-12892, CVE-2020 -12893, CVE-2020-12894, CVE-2020-12895, CVE-2020-12898, CVE-2020-12901, CVE-2020-12903, CVE-2020-12900, CVE-2020-12929, CVE-2020-12960, CVE-2020-12980, CVE-2020-12981, CVE-2020-12982, CVE-2020-12983, CVE-2020-12985, CVE-2020-12962, CVE-2020-12904, CVE-2020-12905, CVE-2020-12920, CVE-2020-12964, CVE-2020-12987, CVE-2020-12920, CVE-2020-12899, CVE-2020-12897, CVE-2020-12963 | Nov 09, 2021 | Mar 04, 2024 |
| AMD-SB-1021 | AMD Server Vulnerabilities – November 2021 | Security Bulletin | CVE-2020-12944, CVE-2020-12946, CVE-2020-12951, CVE-2020-12954, CVE-2020-12961, CVE-2020-12988, CVE-2021-26312, CVE-2021-26315, CVE-2021-26320, CVE-2021-26321, CVE-2021-26322, CVE-2021-26323, CVE-2021-26325, CVE-2021-26326, CVE-2021-26327, CVE-2021-26329, CVE-2021-26330, CVE-2021-26331, CVE-2021-26335, CVE-2021-26336, CVE-2021-26337, CVE-2021-26338, CVE-2020-12951, CVE-2021-26324, CVE-2021-26332, CVE-2021-26351, CVE-2021-26352, CVE-2021-26353, CVE-2021-26370, CVE-2021-26390, CVE-2021-26408, CVE-2021-46771 | Nov 08, 2021 | Mar 04, 2024 |
| AMD-SB-8002 | AMD UltraScale™/UltraScale+™ FPGA Series RSA Authentication | Security Bulletin | CVE-2023-20570 | Feb 13, 2024 | Feb 13, 2024 |
| AMD-SB-3007 | SEV-SNP Firmware Vulnerabilities | Security Bulletin | CVE-2023-31346, CVE-2023-31347 | Feb 13, 2024 | Feb 13, 2024 |
| AMD-SB-5001 | AMD Embedded Processors Vulnerabilities – February 2024 | Security Bulletin | CVE-2020-12930, CVE-2020-12931, CVE-2021-46757, CVE-2022-23820, CVE-2022-23821, CVE-2023-20563, CVE-2023-20565, CVE-2021-46754, CVE-2021-46774, CVE-2023-20533, CVE-2023-20566, CVE-2023-20571, CVE-2021-26345, CVE-2021-46762, CVE-2021-46766, CVE-2022-23830, CVE-2023-20521, CVE-2023-20526, CVE-2021-26392, CVE-2021-26393 | Feb 13, 2024 | Feb 13, 2024 |
| AMD-SB-7011 | AMD SMM Supervisor Vulnerability Security Notice | Security Bulletin | CVE-2023-20596 | Nov 14, 2023 | Jan 16, 2024 |
| AMD-SB-4003 | SMM Memory Corruption Vulnerability | Security Bulletin | CVE-2023-20555 | Aug 08, 2023 | Jan 16, 2024 |
| AMD-SB-3006 | Debug Exception Delivery in Secure Nested Paging | Security Bulletin | CVE-2023-20573 | Jan 09, 2024 | Jan 09, 2024 |
| AMD-SB-6009 | AMD Radeon™ Graphics Kernel Driver Privilege Management Vulnerability | Security Bulletin | CVE-2023-20598 | Oct 16, 2023 | Jan 04, 2024 |
| AMD-SB-1039 | Execution Unit Scheduler Contention Side-Channel Vulnerability on AMD Processors | Security Bulletin | CVE-2021-46778 | Aug 09, 2022 | Dec 18, 2023 |
| AMD-SB-6003 | AMD Graphics Driver Vulnerabilities – November 2023 | Security Bulletin | CVE-2021-46748, CVE-2023-20567, CVE-2023-20568, CVE-2023-31320 | Nov 14, 2023 | Nov 14, 2023 |
| AMD-SB-3005 | AMD INVD Instruction Security Notice | Security Bulletin | CVE-2023-20592 | Nov 14, 2023 | Nov 14, 2023 |
| AMD-SB-3002 | AMD Server Vulnerabilities – Nov 2023 | Security Bulletin | "CVE-2021-26345, CVE-2021-46766, CVE-2021-46774, CVE-2022-23820, CVE-2022-23830, CVE-2023-20519, CVE-2023-20521, CVE-2023-20526, CVE-2023-20533, CVE-2023-20566 " | Nov 14, 2023 | Nov 14, 2023 |
| AMD-SB-4002 | AMD Client Vulnerabilities – November 2023 | Security Bulletin | CVE-2022-23820, CVE-2022-23821, CVE-2023-20563, CVE-2023-20565, CVE-2021-46774, CVE-2023-20533, CVE-2023-20571, CVE-2021-46758, CVE-2021-46766, CVE-2023-20521, CVE-2023-20526 | Nov 14, 2023 | Nov 14, 2023 |
| AMD-SB-4001 | Client Vulnerabilities – May 2023 | Security Bulletin | CVE-2021-26391, CVE-2021-26392, CVE-2021-26393, CVE-2021-26354, CVE-2021-26371, CVE-2021-46760, CVE-2021-46773, CVE-2021-46756, CVE-2021-46753, CVE-2021-46754, CVE-2021-26365, CVE-2021-26356, CVE-2021-26406, CVE-2021-46749, CVE-2021-46755, CVE-2021-46792, CVE-2021-46794, CVE-2021-46765, CVE-2021-46759 | May 09, 2023 | Aug 25, 2023 |
| AMD-SB-7004 | AMD Ryzen™ Master Security Bulletin | Security Bulletin | CVE-2023-20564, CVE-2023-20560 | Aug 08, 2023 | Aug 23, 2023 |
| AMD-SB-1052 | AMD Ryzen™ Master Security Bulletin | Security Bulletin | CVE-2022-27677 | Feb 14, 2023 | Aug 08, 2023 |
| AMD-SB-4005 | fTPM Voltage Fault Injection | Security Bulletin | CVE-2023-20589 | Aug 08, 2023 | Aug 08, 2023 |
| AMD-SB-6007 | Radeon™ Software Crimson ReLive Edition | Security Bulletin | CVE-2023-20586 | Aug 08, 2023 | Aug 08, 2023 |
| AMD-SB-7007 | Speculative Leaks Security Notice | Security Bulletin | CVE-2023-20588 | Aug 08, 2023 | Aug 08, 2023 |
| AMD-SB-7001 | OpenSSL Vulnerabilities | Security Bulletin | CVE-2022-3602, CVE-2022-3786 | Aug 08, 2023 | Aug 08, 2023 |
| AMD-SB-7003 | AMD μProf Security Bulletin | Security Bulletin | CVE-2023-20562, CVE-2023-20556, CVE-2023-20561 | Aug 08, 2023 | Aug 08, 2023 |
| AMD-SB-7006 | Software based Power Side Channel on AMD CPUs | Security Bulletin | CVE-2023-20583 | Aug 01, 2023 | Aug 01, 2023 |
| AMD-SB-3004 | AMD SEV VM Power Side Channel Security Bulletin | Security Bulletin | CVE-2023-20575 | Jul 11, 2023 | Jul 11, 2023 |
| AMD-SB-3001 | AMD Server Vulnerabilities – May 2023 | Security Bulletin | CVE-2021-26354, CVE-2021-26356, CVE-2021-26371, CVE-2021-26379, CVE-2021-26406, CVE-2021-46756, CVE-2021-46763, CVE-2021-46764, CVE-2021-46769, CVE-2021-46762, CVE-2023-20524, CVE-2021-26397, CVE-2022-23818, CVE-2021-46755 | May 09, 2023 | May 09, 2023 |
| AMD-SB-7002 | TPM Out of Bounds Access | Security Bulletin | CVE-2023-1018, CVE-2023-1017 | Apr 11, 2023 | Apr 11, 2023 |
| AMD-SB-1045 | Cross-Thread Return Address Predictions | Security Bulletin | CVE-2022-27672 | Feb 14, 2023 | Feb 14, 2023 |
| AMD-SB-1032 | AMD Server Vulnerabilities – January 2023 | Security Bulletin | CVE-2021-26316, CVE-2021-26398, CVE-2021-26402, CVE-2021-39298, CVE-2021-26328, CVE-2021-26343, CVE-2021-26355, CVE-2021-26353, CVE-2021-26396, CVE-2021-26403, CVE-2021-26407, CVE-2021-26409, CVE-2021-46779, CVE-2021-46791, CVE-2022-23813, CVE-2022-23814, CVE-2023-20529, CVE-2023-20530, CVE-2023-20531, CVE-2021-26404, CVE-2021-46767, CVE-2021-46768, CVE-2023-20522, CVE-2023-20523, CVE-2023-20525, CVE-2023-20527, CVE-2023-20528, CVE-2023-20532 | Jan 10, 2023 | Jan 10, 2023 |
| AMD-SB-1031 | AMD Client Vulnerabilities – January 2023 | Security Bulletin | CVE-2021-26316, CVE-2021-26346, CVE-2021-46795 | Jan 10, 2023 | Jan 10, 2023 |
| AMD-SB-1040 | IBPB and Return Stack Buffer Interactions | Security Bulletin | CVE-2022-23824 | Nov 08, 2022 | Dec 06, 2022 |
| AMD-SB-1047 | AMD Link Android App | Security Bulletin | CVE-2022-27673 | Nov 08, 2022 | Nov 08, 2022 |
| AMD-SB-1029 | AMD Graphics Driver Vulnerabilities – November 2022 | Security Bulletin | CVE-2020-12930, CVE-2020-12931, CVE-2021-26360, CVE-2021-26391, CVE-2021-26392, CVE-2021-26393 | Nov 08, 2022 | Nov 08, 2022 |
| AMD-SB-1046 | AMD μProf Security Bulletin | Security Bulletin | CVE-2022-23831, CVE-2022-27674 | Nov 08, 2022 | Nov 08, 2022 |
| AMD-SB-1037 | AMD CPU Branch Type Confusion | Security Bulletin | CVE-2022-23825, CVE-2022-29900 (aka CVE-2022-23816) | Jul 12, 2022 | Jul 14, 2022 |
| AMD-SB-1038 | Frequency Scaling Timing Power Side-Channels | Security Bulletin | CVE-2022-23823 | Jun 14, 2022 | Jul 12, 2022 |
| AMD-SB-1033 | Ciphertext Side Channels on AMD SEV | Security Bulletin | CVE-2021-46744 | May 10, 2022 | May 10, 2022 |
| AMD-SB-1035 | Speculative Load Disordering | Security Bulletin | CVE-2021-26400 | May 10, 2022 | May 10, 2022 |
| AMD-SB-1027 | AMD Client Vulnerabilities – May 2022 | Security Bulletin | CVE-2021-26317, CVE-2021-26335, CVE-2021-39298, CVE-2023-20558, CVE-2023-20559, CVE-2021-26373, CVE-2020-12946, CVE-2021-26361, CVE-2021-26363, CVE-2021-26366, CVE-2021-26369, CVE-2021-26386, CVE-2021-26336, CVE-2021-26337, CVE-2020-12951, CVE-2021-26376, CVE-2021-26352 , CVE-2021-26375, CVE-2021-26378, CVE-2021-26372, CVE-2021-26351, CVE-2021-26390, CVE-2021-26362, CVE-2021-26339, CVE-2020-12944, CVE-2021-26368, CVE-2021-26388, CVE-2021-26312, CVE-2021-26384, CVE-2021-26382 | May 10, 2022 | May 10, 2022 |
| AMD-SB-1028 | AMD Server Vulnerabilities - May 2022 | Security Bulletin | CVE-2021-26312, CVE-2021-26342, CVE-2021-26347, CVE-2021-26350, CVE-2021-26364, CVE-2021-26372, CVE-2021-26373, CVE-2021-26375, CVE-2021-26376, CVE-2021-26378, CVE-2021-26388, CVE-2021-26339, CVE-2021-26348, CVE-2021-26349 | May 10, 2022 | May 10, 2022 |
| AMD-SB-1026 | AMD CPUs May Transiently Execute Beyond Unconditional Direct Branch | Security Bulletin | CVE-2021-26341 | Mar 08, 2022 | Mar 08, 2022 |
| AMD-SB-1036 | LFENCE/JMP Mitigation Update for CVE-2017-5715 | Security Bulletin | CVE-2021-26401 | Mar 08, 2022 | Mar 08, 2022 |
| AMD-SB-1034 | AMD Response to Log4j (Log4Shell) Vulnerability | Security Bulletin | CVE-2021-44228 | Dec 15, 2021 | Jan 17, 2022 |
| AMD-SB-1009 | AMD Chipset Driver Information Disclosure Vulnerability | Security Bulletin | CVE-2021-26333 | Nov 14, 2021 | Nov 14, 2021 |
| AMD-SB-1016 | Potential Improper Access Control Vulnerability in AMD μProf Tool | Security Bulletin | CVE-2021-26334 | Nov 09, 2021 | Nov 09, 2021 |
| AMD-SB-1017 | Side-channels Related to the x86 PREFETCH Instruction | Security Bulletin | CVE-2021-26318 | Oct 12, 2021 | Oct 12, 2021 |
| AMD-SB-1010 | Transient Execution of Non-canonical Accesses | Security Bulletin | CVE-2020-12965 | Aug 10, 2021 | Aug 10, 2021 |
| AMD-SB-1013 | AMD Secure Encryption Virtualization (SEV) Information Disclosure | Security Bulletin | CVE-2020-12966 | Aug 10, 2021 | Aug 10, 2021 |
| AMD-SB-1023 | TLB Poisoning Attacks on AMD Secure Encrypted Virtualization (SEV) | Security Bulletin | CVE-2021-26340 | Jun 12, 2021 | Jun 12, 2021 |
| AMD-SB-1003 | Speculative Code Store Bypass and Floating-Point Value Injection | Security Bulletin | CVE-2021-26313, CVE-2021-26314 | Jun 08, 2021 | Jun 08, 2021 |
| AMD-SB-1004 | AMD Secure Encrypted Virtualization | Security Bulletin | CVE-2020-12967, CVE-2021-26311 | May 11, 2021 | May 11, 2021 |
| AMD-SB-1006 | AMD RESPONSE TO “I see dead µops: leaking secrets via Intel/AMD micro-op caches” RESEARCH PAPER | Security Bulletin | N/A | May 04, 2021 | May 04, 2021 |
Vulnerability Disclosure Policy
At AMD, we treat potential security vulnerabilities seriously and seek to respond swiftly and comprehensively. From inception to production, AMD aims to incorporate security features into its products, and we actively review for potential security vulnerabilities. AMD is committed to working across the ecosystem, including customers, vendors, academics, researchers, and users, to provide a secure computing environment.
Scope
The AMD Vulnerability Disclosure Policy covers AMD APUs, CPUs, NPUs, IPUs, DPUs, GPUs, FPGAs, and software.
We encourage well-researched reports that focus on real-world security threats, including a PoC (Proof of Concept) with minimal dependencies. Reported issues requiring physical access to the system to exploit are out of scope in some situations.
AMD encourages finding and reporting potential security vulnerabilities through our Bug Bounty program for individuals who:
- Conduct research that does not harm AMD or our customers
- Test within the scope of this Vulnerability Disclosure Policy (VDP)
- Adhere to the applicable laws both in their location and the United States
- Refrain from disclosing vulnerability details before a mutually agreed-upon date
- Test on eligible AMD branded products and technologies that are in scope of the Program
Reports may also be submitted directly to psirt@amd.com.
How to Submit a Vulnerability Report
Reports can be submitted via 2 methods:
- AMD Bug Bounty Program
The AMD Bug Bounty Program is a collaboration between AMD and the research community. AMD believes that collaboration with security researchers and promoting security research is an important step in helping to improve the security of AMD products. We encourage security researchers to work with us to help mitigate and coordinate the disclosure of potential security vulnerabilities and look forward to working with you! Refer to AMD Bug Bounty Program for more details.
To report a vulnerability, please submit your report through our provider, Intigriti.
- Report Directly to AMD
To report a potential security vulnerability in any AMD product and/or technology, please email your report* to the AMD Product Security Team at psirt@amd.com. Encryption is not required, but if preferred, you can see our public key below. Please note AMD follows Coordinated Vulnerability Disclosure (CVD) and expects all security researchers who submit reports to do the same.
*Reports should contain the following information to allow for efficient triage and analysis:
- Well-researched reports in English
- Product name, including software or firmware version
- Reports that include proof-of-concept code
- Description of how the issue was found, the impact and any potential remediation
- Plans or intentions for public disclosure
Note any missing information may cause delays in our ability to address the vulnerability. Security researchers who submit a validated report and follow CVD will be given credit in our published security bulletin.
What You Can Expect From AMD
The AMD Product Security Incident Response Team (PSIRT) is the focal point for reporting potential AMD product security issues; AMD PSIRT interfaces with the product security ecosystem, including security researchers, industry peers, government organizations, customers, and vendors, working together to report potential AMD product security issues.
The PSIRT team, working with various teams within AMD, follows the following high-level process:
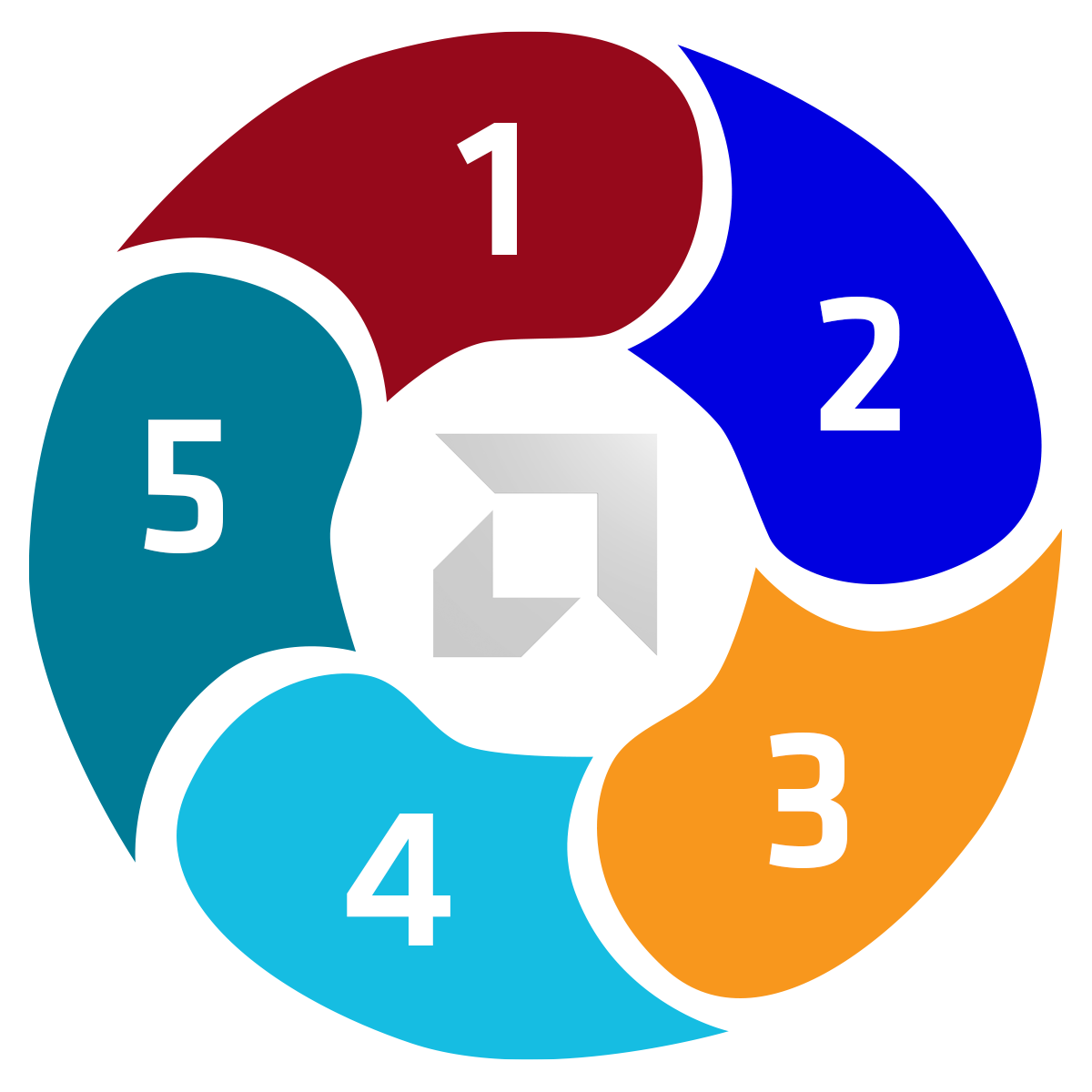

Triage
Review submitted information, logs issue and assigns ticket ID, and identifies appropriate engineering team(s).

Analysis
Validates issues determining severity, impact and criticality.

Remediate
If remediation is required works with business units and product development to define approach and plans.

Disclosure
Appropriate notification to affected customers and/or issuance of public security bulletin.

Review
Leverage feedback from customers, researchers and internal teams to further improve product security.
Cycle Time for Mitigation
As an upstream provider and participant in Coordinated Vulnerability Disclosure (CVD), AMD requires sufficient time between the initial report and public disclosure.
Some issues may require AMD to provide a mitigation to our customers, who will then integrate, and ship patched products. Other issues may require a coordinated approach where certain aspects of a mitigation may be addressed by AMD and other aspects addressed by various eco-system vendors. In all cases, AMD works to integrate any needed changes and validate mitigations while coordinating any associated disclosures.
Disclosure timeliness is determined on an issue-by-issue basis, appropriate to the situation, and with protection of the end-user in mind. In some cases, disclosure may be completed in the common embargo time period of 90 days. In most cases, however, due to eco-system and product complexity, mitigations can take longer to develop, integrate, and provide to end-users. In these cases, a longer embargo period is needed to allow vendors and partners to adequately patch systems.
- 2021
- 2020
- 2019
- 2018
3/26/21
Predictive Store Forwarding
https://community.amd.com/t5/amd-business-blog/predictive-store-forwarding/ba-p/456422
UPDATED 2/24/21 (originally posted 11/10/2020)
RAPL (CVE-2020-12912)
In a paper titled, "PLATYPUS: Software-based Power Side-Channel Attacks on x86", researchers from Graz University of Technology and CISPA Helmholtz Center for Information Security describe a differential power analysis method to use the Linux-based Running Average Power Limit (RAPL) interface to show various side channel attacks.
In line with industry partners, AMD has updated the RAPL interface to require privileged access. The change is in the process of being integrated into Linux distributions.
TPM Vulnerability - Non orderly shutdown failed tries (CVE-2020 12926)
AMD was notified by the Trusted Computing Group (TCG) that its Trusted Platform Modules (TPM) reference software may not properly track the number of times a failed shutdown happens. This can leave the TPM in a state where confidential key material in the TPM may be able to be compromised. AMD believes that the attack requires physical access of the device because the power must be repeatedly turned on and off. This potential attack may be used to change confidential information, alter executables signed by key material in the TPM, or create a denial of service of the device.
AMD has provided mitigations to motherboard vendors.
Privilege Escalation in atillk64.sys (CVE-2020-12927)
A researcher (h0mbre pwner) notified AMD of a potential vulnerability in a driver created with the AMD VBIOS Flash Tool Software Development Kit (SDK). The disclosed vulnerability may allow low privileged users to potentially escalate privilege to administrator privileges on Windows. The potential vulnerability is in the AMD VBIOS Flash Tool Software Development Kit (SDK) used by customers to create drivers. AMD has provided mitigations in the AMD VBIOS Flash Tool Software Development Kit (SDK) 3.12.
Escape Handler (CVE-2020-12933)
10/13/2020
Our ecosystem collaborator Cisco Talos has published a new potential vulnerability in AMD graphics drivers, which may result in a blue screen. The issue was addressed in Radeon™ Software Adrenalin 2020 Edition available here.
AMD believes that confidential information and long-term system functionality are not impacted, and users can resolve the issue by restarting the computer.
A specially crafted D3DKMTEscape request can cause an out-of-bounds read in Windows OS kernel memory area. This vulnerability can be triggered from a non-privileged account.
We thank the researchers for their ongoing collaboration and coordinated disclosure. More information on their research can be found on the Cisco Talos website.
AMD Ryzen Master™ Driver Vulnerability (CVE-2020-12928)
10/13/2020
A researcher has discovered a potential security vulnerability impacting AMD Ryzen™ Master that may allow authenticated users to elevate from user to system privileges. AMD has released a mitigation in AMD Ryzen Master 2.2.0.1543. AMD believes that the attack must come from a non-privileged process already running on the system when the local user runs AMD Ryzen™ Master and that a remote attack has not been demonstrated. The latest version of the software is available for download at https://www.amd.com/en/technologies/ryzen-master.
We thank the researcher for the ongoing collaboration and coordinated disclosure.
CreateAllocation (CVE-2020-12911)
10/7/2020
Our ecosystem collaborator Cisco Talos has published a new potential vulnerability in AMD graphics drivers, which may result in a blue screen. AMD believes that confidential information and long-term system functionality are not impacted, and that the user can resolve the issue by restarting the computer. AMD plans to issue updated graphics drivers to address the issue in the first quarter of 2021.
The research finds that a specially crafted D3DKMTCreateAllocation API request can cause an out-of-bounds read and denial of service (BSOD). This vulnerability can be triggered from non-privileged accounts.
We thank the researchers for their ongoing collaboration and coordinated disclosure. More information on their research can be found on the Cisco Talos website.
Pixel Shader on Hyper-V (CVE-2020-6100, CVE-2020-6101, CVE-2020-6102, CVE-2020-6103)
7/14/20
New research from our ecosystem collaborator Cisco Talos explores potential vulnerabilities in a specific virtual machine (VM) configuration using AMD GPU or APU processors. AMD will issue updated graphics drivers to help remediate the issues in September 2020.
The research finds that on a compromised Windows guest Microsoft Hyper-V VM based on an AMD GPU or APU with an AMD graphics driver installed and with Microsoft’s RemoteFX 3D feature enabled, an attacker could potentially pass maliciously malformed pixel shaders and gain access to a host machine.
RemoteFX 3D is a Microsoft feature that was previously discontinued as a new feature for VMs running Windows 10 in 2018 and in Windows Server in 2019. On July 14, 2020, Microsoft released an advisory announcing the immediate disabling and eventual removal of its RemoteFX 3D feature.
AMD will issue updated graphics drivers to remediate these issues for existing VMs that use the RemoteFX 3D feature in September 2020 on the AMD Support webpage for AMD customers that purchased an AMD GPU or APU. For original equipment manufacturer (OEM) and add-in-board (AIB) products, AMD recommends users contact the manufacturer.
We thank the researchers for their ongoing collaboration and coordinated disclosure. More information on their research can be found on the Cisco Talos website.
SMM Callout Privilege Escalation (CVE-2020-12890)
6/17/20
AMD is aware of new research related to a potential vulnerability in AMD software technology supplied to motherboard manufacturers for use in their Unified Extensible Firmware Interface (UEFI) infrastructure and plans to complete delivery of updated versions designed to mitigate the issue by the end of June 2020.
The targeted attack described in the research requires privileged physical or administrative access to a system based on select AMD notebook or embedded processors. If this level of access is acquired, an attacker could potentially manipulate the AMD Generic Encapsulated Software Architecture (AGESA) to execute arbitrary code undetected by the operating system.
AMD believes this only impacts certain client and embedded APU processors launched between 2016 and 2019. AMD has delivered the majority of the updated versions of AGESA to our motherboard partners and plans to deliver the remaining versions by the end of June 2020. AMD recommends following the security best practice of keeping devices up-to-date with the latest patches. End users with questions about whether their system is running on these latest versions should contact their motherboard or original equipment/system manufacturer.
We thank Danny Odler for his ongoing security research.
TRRespass (CVE-2020-10255)
UPDATED 5/22/20 (originally posted 3/10/20)
AMD is aware of new research related to an industry-wide DRAM issue called TRRespass whereby researchers demonstrated a method that claims to bypass existing Targeted Row Refresh (TRR) mitigations. AMD microprocessor products include memory controllers designed to meet industry-standard DDR specifications, and we have enabled platform providers with an expanded set of controls that can be configured into their BIOS’ in consultation with DRAM vendors. Susceptibility varies based on DRAM device, vendor, technology and system settings.
AMD recommends contacting the DRAM or system manufacturer to determine any susceptibility to this issue, in addition to enabling existing DRAM mitigations that reduce a system’s susceptibility to Row Hammer-style attacks like TRRespass, including:
- Using DRAM supporting Error Correcting Codes (ECC)
- Using DRAM and memory controllers supporting Targeted Row Refresh (TRR)
- Using memory refresh rates above 1x
- Using AMD CPUs with memory controllers that support a Maximum Activate Count (MAC)
We thank the researchers for their collaboration and participating in the industry best practice of coordinated disclosure. For more information on their research, visit their website.
Take A Way
3/7/20
We are aware of a new white paper that claims potential security exploits in AMD CPUs, whereby a malicious actor could manipulate a cache-related feature to potentially transmit user data in an unintended way. The researchers then pair this data path with known and mitigated software or speculative execution side channel vulnerabilities. AMD believes these are not new speculation-based attacks.
AMD continues to recommend the following best practices to help mitigate against side-channel issues:
- Keeping your operating system up-to-date by operating at the latest version revisions of platform software and firmware, which include existing mitigations for speculation-based vulnerabilities
- Following secure coding methodologies
- Implementing the latest patched versions of critical libraries, including those susceptible to side channel attacks
- Utilizing safe computer practices and running antivirus software
Shader Functionality Remote Code Execution (CVE-2019-5049, CVE-2019-5098, CVE-2019-5146, CVE-2019-5147, CVE-2019-5124, CVE-2019-5183)
UPDATED 1/27/20 and 12/3/19 to add new CVE# (originally posted 9/16/19)
Through ongoing collaboration with industry partners, AMD became aware of a potential vulnerability in a specific virtual machine application when using an AMD GPU or APU and has delivered an updated graphics driver to remediate the exploit.
The specific conditions of this exploit require a virtual machine with an AMD GPU or APU running VMware Workstation Pro on a compromised guest Windows OS. Under these conditions, an attacker could modify a compiled shader and use it to expose sensitive user information. AMD updated the kernel mode driver code in its graphics drivers starting with version 19.8.1 to remediate this application exploit.
The updated graphics drivers are available on the AMD Support webpage for AMD customers that purchased an AMD GPU or APU. For original equipment manufacturer (OEM) and add-in-board (AIB) products, AMD recommends users contact the manufacturer.
We thank Cisco Talos for their collaboration on this matter and allowing us the necessary time to prepare mitigations. For more information, visit their website.
Screwed Drivers
8/11/19
At AMD, security is a top priority. We were made aware of the public disclosure of potential industry-wide, driver-related vulnerabilities on August 11, 2019 and, after gaining new information from the researcher, AMD now believes this is related to a disclosure communicated to us earlier this year regarding the AMDVBFlash graphics driver tool that was temporarily made available on our website so early adopters of older AMD graphics products could perform a needed Video BIOS refresh and has since been removed. AMD is continuing to investigate the issue to determine if any other of our drivers may be affected.
SWAPGS (CVE-2019-1125)
8/6/19
AMD is aware of new research claiming new speculative execution attacks that may allow access to privileged kernel data. Based on external and internal analysis, AMD believes it is not vulnerable to the SWAPGS variant attacks because AMD products are designed not to speculate on the new GS value following a speculative SWAPGS. For the attack that is not a SWAPGS variant, the mitigation is to implement our existing recommendations for Spectre variant 1.
Specific details by published description:
Description |
AMD Recommendation |
SWAPGS instruction speculation at CPL3 (Scenario 1) |
AMD believed not impacted |
SWAPGS instruction speculation at CPL0 (Scenario 2, Variant 1) |
AMD believed not impacted |
GS base value speculation (Scenario 2, Variant 2) |
AMD recommends implementing existing mitigations for Spectre variant 1 |
Secure Encrypted Virtualization Invalid ECC Curve Points (CVE-2019-9836)
6/25/19
At AMD, security remains a top priority and we continue to work to identify any potential risks for our customers. Through ongoing collaboration with industry researchers AMD became aware that, if using the user-selectable AMD secure encryption feature on a virtual machine running the Linux operating system, an encryption key could be compromised by manipulating the encryption technology’s behavior. AMD released firmware-based cryptography updates to our ecosystem partners and on the AMD website to remediate this risk.
RamBleed (CVE-2019-0174)
6/12/19
Researchers reported a new vulnerability called RamBleed that exploits the electrical interaction between close-packed DDR3 and DDR4 DRAM circuitry to potentially expose kernel privileges and confidential information. Based on our internal analysis, AMD believes the industry-known mitigations for RowHammer, in addition to AMD Secure Memory Encryption (SME) and AMD Secure Encrypted Virtualization (SEV), protect against RamBleed.
Previous RowHammer Guidance
The RowHammer issue identified in the Google release is an industry-wide DRAM issue that affects DRAMs manufactured on newer process technologies that are not designed to address this issue. AMD microprocessor products include memory controllers designed to meet industry-standard DDR specifications.
The possibility of this issue happening on a system depends on the DRAM in the system. Susceptibility to this issue varies by DRAM vendor, technology, and DRAM device. Contact your system vendor to see if you have susceptible DRAM.
Mitigations include:
- Upgrade the system BIOS to double the refresh rate to reduce the error rate; or
- Use memory manufactured on older and unaffected technologies or newer memory that has design fixes to address this problem and upgrade your BIOS to recognize the newer memory.
Fallout, Rogue In-Flight Data Load (RIDL), and ZombieLoad Attack (CVE-2018-12126, CVE-2018-12130, CVE-2018-12127, CVE-2019-11091)
5/14/19
At AMD we develop our products and services with security in mind. Based on our analysis and discussions with the researchers, we believe our products are not susceptible to ‘Fallout’, ‘RIDL’ or ‘ZombieLoad Attack’ because of the hardware protection checks in our architecture. We have not been able to demonstrate these exploits on AMD products and are unaware of others having done so.
For more information, see our new white paper, titled “Speculation Behavior in AMD Micro-Architectures.”
SPOILER (CVE-2019-0162)
3/15/19
We are aware of the report of a new security exploit called SPOILER which can gain access to partial address information during load operations. The SPOILER exploit can gain access to partial address information above address bit 11 during load operations. AMD processors do not use partial address matches above address bit 11 when resolving load conflicts.
SplitSpectre
12/6/18
AMD is aware of the latest research published claiming new approaches to speculative execution attacks called SplitSpectre. AMD believes the mitigation is to implement our existing speculative execution recommendations.
PortSmash (CVE-2018-5407)
11/27/18
AMD does not believe the PortSmash issue (https://seclists.org/oss-sec/2018/q4/123) is related to previously found speculative execution issues like Spectre. Instead, AMD believes the issues are related to any processor that uses simultaneous multithreading (SMT), including those from AMD, that is vulnerable to software that exposes the activity of one process to another running on the same processor. We believe this issue can be mitigated in software by using side-channel counter measures. For example, OpenSSL, which was used in the researcher’s proof of concept, has already been updated to address this type of attack.
AMD Response to Systematic Evaluations of Transient Execution Variants
11/13/18
AMD is aware of the latest research published claiming new speculative execution attacks. AMD believes it is not vulnerable to some of these attacks because of the hardware paging architecture protections in AMD devices and, for those that are not solved by our paging architecture protections, the mitigation is to implement our existing recommendations.
Specific recommendations by published description:
New Variants of Spectre v1 – AMD recommends implementing existing mitigations
- Pattern History Table - Cross Address - Out of Place (PHT-CA-OP)
- Pattern History Table - Cross Address - In Place (PHT-CA-IP)
- Pattern History Table - Same Address - Out of Place (PHT-SA-OP)
New Variants of Spectre v2 – AMD recommends implementing existing mitigations
- Branch Target Buffer - Same Address - In Place (BTB-SA-IP)
- Branch Target Buffer - Same Address - Out of Place (BTB-SA-OP)
New Variant of Meltdown
- Meltdown-BK – AMD believes this does not affect its platforms because AMD does not have this feature in its products
New Variant of Spectre v1 – referred by researchers as a Meltdown variant
- Meltdown-BD – AMD believes 32-bit systems using the BOUND instruction may be impacted and recommends implementing existing mitigations for Spectre v1 for such systems.
2018 Firmware TPM Updates
9/26/18
Earlier this year, AMD disclosed mitigations related to potential security vulnerabilities for AMD firmware Trusted Platform Module (fTPM) versions v.96, v1.22, and v1.37. AMD believes the fTPM vulnerabilities only apply to some of its client processors as fTPM is not enabled on AMD server, graphics and embedded products. AMD has delivered a patch to PC manufacturers to address the issue.
Microsoft Windows users can verify their fTPM version and find instructions to clear the TPM at: https://docs.microsoft.com/en-us/windows/device-security/tpm/initialize-and-configure-ownership-of-the-tpm
AMD has recommended that PC manufacturers qualify and release an updated BIOS integrating the fTPM patch, as appropriate, into production at the next available opportunity and provide guidance to end users to apply fixes as defined based on the product. For fTPM v1.37, AMD has notified PC manufacturers that they should consider updating the system BIOS ahead of clearing the fTPM to help protect generated platform-level keys.
AMD recommends users contact their PC manufacturer for platform-specific instructions as a part of following best security practices to keep devices up-to-date with the latest patches.
Foreshadow (CVE-2018-3615, CVE-2018-3620, CVE-2018-3646)
8/14/18 – Updated
As in the case with Meltdown, we believe our processors are not susceptible to these new speculative execution attack variants: L1 Terminal Fault – SGX (also known as Foreshadow) CVE 2018-3615, L1 Terminal Fault – OS/SMM (also known as Foreshadow-NG) CVE 2018-3620, and L1 Terminal Fault – VMM (also known as Foreshadow-NG) CVE 2018-3646, due to our hardware paging architecture protections. We are advising customers running AMD EPYC™ processors in their data centers, including in virtualized environments, to not implement Foreshadow-related software mitigations for their AMD platforms.
Spectre Mitigation Update
7/13/18
This week, a sub-variant of the original, Google Project (GPZ) variant 1 / Spectre security vulnerability was disclosed by MIT. Consistent with variant 1, we believe this threat can be mitigated through the operating system (OS). AMD is working with the software ecosystem to mitigate variant 1.1 through operating system updates where necessary. We have not identified any AMD x86 products susceptible to the Variant 1.2 vulnerability in our analysis to-date. Please check with your OS provider for the latest information.
AMD has also updated related portions of the Software Techniques for Managing Speculation on AMD Processors white paper.
TLBleed
7/12/18
Based on our analysis to date we have not identified any AMD products that are vulnerable to TLBleed side channel attack identified by researchers. Security remains a top priority and we will continue to work to identify any potential risks for our customers and, if needed, potential mitigations.
LazyFPU (CVE-2018-3665)
6/18/18
Based on our analysis to date, because of our unique processor implementation we currently do not believe our products are susceptible to the resent security vulnerability identified around lazy FPU switching
“Speculative Store Bypass” Vulnerability Mitigations for AMD Platforms
5/21/18
Today, Microsoft and Google Project Zero researchers have identified a new category of speculative execution side channel vulnerability (Speculative Store Bypass or SSB) that is closely related to the previously disclosed GPZ/Spectre variant 1 vulnerabilities. Microsoft has released an advisory on the vulnerability and mitigation plans.
AMD recommended mitigations for SSB are being provided by operating system updates back to the Family 15 processors (“Bulldozer” products). For technical details, please see the AMD white paper. Microsoft is completing final testing and validation of AMD-specific updates for Windows client and server operating systems, which are expected to be released through their standard update process. Similarly, Linux distributors are developing operating system updates for SSB. AMD recommends checking with your OS provider for specific guidance on schedules.
Based on the difficulty to exploit the vulnerability, AMD and our ecosystem partners currently recommend using the default setting that maintains support for memory disambiguation.
We have not identified any AMD x86 products susceptible to the Variant 3a vulnerability in our analysis to-date.
As a reminder, security best practices of keeping your operating system and BIOS up-to-date, utilizing safe computer practices and running antivirus software are always the first line of defense in maintaining device security.
Spectre Mitigation Update
4/10/18 (Updated 5/8/18 to reflect Microsoft release of Windows Server 2016)
Today, AMD is providing updates regarding our recommended mitigations for Google Project Zero (GPZ) Variant 2 (Spectre) for Microsoft Windows users. These mitigations require a combination of processor microcode updates from our OEM and motherboard partners, as well as running the current and fully up-to-date version of Windows. For Linux users, AMD recommended mitigations for GPZ Variant 2 were made available to our Linux partners and have been released to distribution earlier this year.
As a reminder, GPZ Variant 1 (Spectre) mitigation is provided through operating system updates that were made available previously by AMD ecosystem partners. GPZ Variant 3 (Meltdown) does not apply to AMD because of our processor design.
While we believe it is difficult to exploit Variant 2 on AMD processors, we actively worked with our customers and partners to deploy the above described combination of operating system patches and microcode updates for AMD processors to further mitigate the risk. A white paper detailing the AMD recommended mitigation for Windows is available, as well as links to ecosystem resources for the latest updates.
Operating System Updates for GPZ Variant 2/Spectre
Microsoft is releasing an operating system update containing Variant 2 (Spectre) mitigations for AMD users running Windows 10 (version 1709) today. Support for these mitigations for AMD processors in Windows Server 2016 is expected to be available following final validation and testing. (Note: May 8, 2018 Microsoft released an operating system update for Windows Server 2016.)
AMD Microcode Updates for GPZ Variant 2/Spectre
In addition, microcode updates with our recommended mitigations addressing Variant 2 (Spectre) have been released to our customers and ecosystem partners for AMD processors dating back to the first “Bulldozer” core products introduced in 2011.
AMD customers will be able to install the microcode by downloading BIOS updates provided by PC and server manufacturers and motherboard providers. Please check with your provider for the latest updates.
We will provide further updates as appropriate on this site as AMD and the industry continue our collaborative work to develop solutions to protect users from security threats.
